The Next Gen Skype Meetings No Sign Up No Client Meetings
Microsoft keeps rolling out new features in the Skype product and I just got a moment to play with some of the new Skype meeting features, which are quite impressive. The features I will underscore:
Frictionless Meetings with No Sign-Up/Login Whatsoever Directly from a Browser
Just go to www.skype.com and click on �Start a conversation� (Note: make sure you are not logged into your Microsoft account to see pure guest functionality.) Type in a name for yourself, and the meeting is in progress.
Nice Chat/Audio/Video Meeting Functionality�Without a Login
From playing with it the functionality seems quite nice. The guest user who sets up the meeting is the Admin and can do quite a bit:
- 1-name the meeting
- 2-Just give anyone an URL and they can join without a login as well
- 3-toggle whether you want to hear notification on each IM
- 4-make chat history available for new joiners
- 5-Easily toggle allowing new people join (toggling this off means no one can join while it is off, but as soon as you toggle it on the original join URL works again)
- 6-remove a user from the group/meeting
- 7-change the picture for the meeting
What is the Capacity?
I was in a meeting that Tom Warren started and noticed that at that time there were 499 participants! (I noticed on the webpage I would get some script timeouts, not sure if my pc needs a reboot or not)
Note, the above was a chat (instant message) meeting only.
Edge Browser Seems to Need No Plugin for Audio/Video
IE and Chrome do.
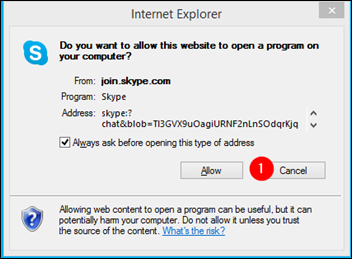
How to Easily Avoid Joining Using the Skype Client?
Just cancel the browser request to use the Skype client
Then click �Join Conversation� on the web page
What Collaboration Methods are supported?
- Video
- Group Chat
- Voice
- Share Photos and Files
- Send Emoticons & Mojis
Note: Desktop sharing is not supported.
Conclusion
I�m impressed. It would be quite cool to have an API where you could do an http post and give your name and it would return the meeting URL. But in any event, this is nice functionality.
Try it yourself in a minute: Just go to www.skype.com and click on �Start a conversation��
download file now